Third party cookie is the key instrument of an internet ad. Ad networks use them to show ads based on users' interests and preferences. Advertisers use them to get new customers.
Just recently browsers have started to ban third party cookies. In this article we tell about technologies that can replace cookie files now: Entity Tag, Fingerprint and ID5. We will show why we preferred using ETag based on our client’s case.
In briefe
-
01
Customer
Ad network uses third party cookies for ad personalization
-
02
Problem
Browsers ban third party cookies
-
03
Task
Find personalized data collection technology which doesn’t use cookie files
-
04
Solution
- Ad network collects users' data with the help of ETag
- Users can’t delete such cookies
- This solution can be quickly implemented and used
- Only unique identifier needs to be found, other user’s data is stored on the servers
Ad network needs third party cookies to show relevant ads
Ad network profits from placing ads on site-publishers. It gets reward from advertisers for each click, ad showing or conversion. The more users are interested in the ad, the more money a network will make.
In order to show ads that would interest users, an ad network needs as much information as possible about them: which products they looked for, which city they’re in, which ads they click the most. For example, if someone has pets then probably, they would be interested in pet supplies. The cookie files are usually used to collect users' information.
The information collected this way is stored on the ad network servers which is linked to the unique user’s identifier or ID. It’s assigned to every user the very first time they visit the site. In the future, ad network will recognize a specific user precisely by his ID.
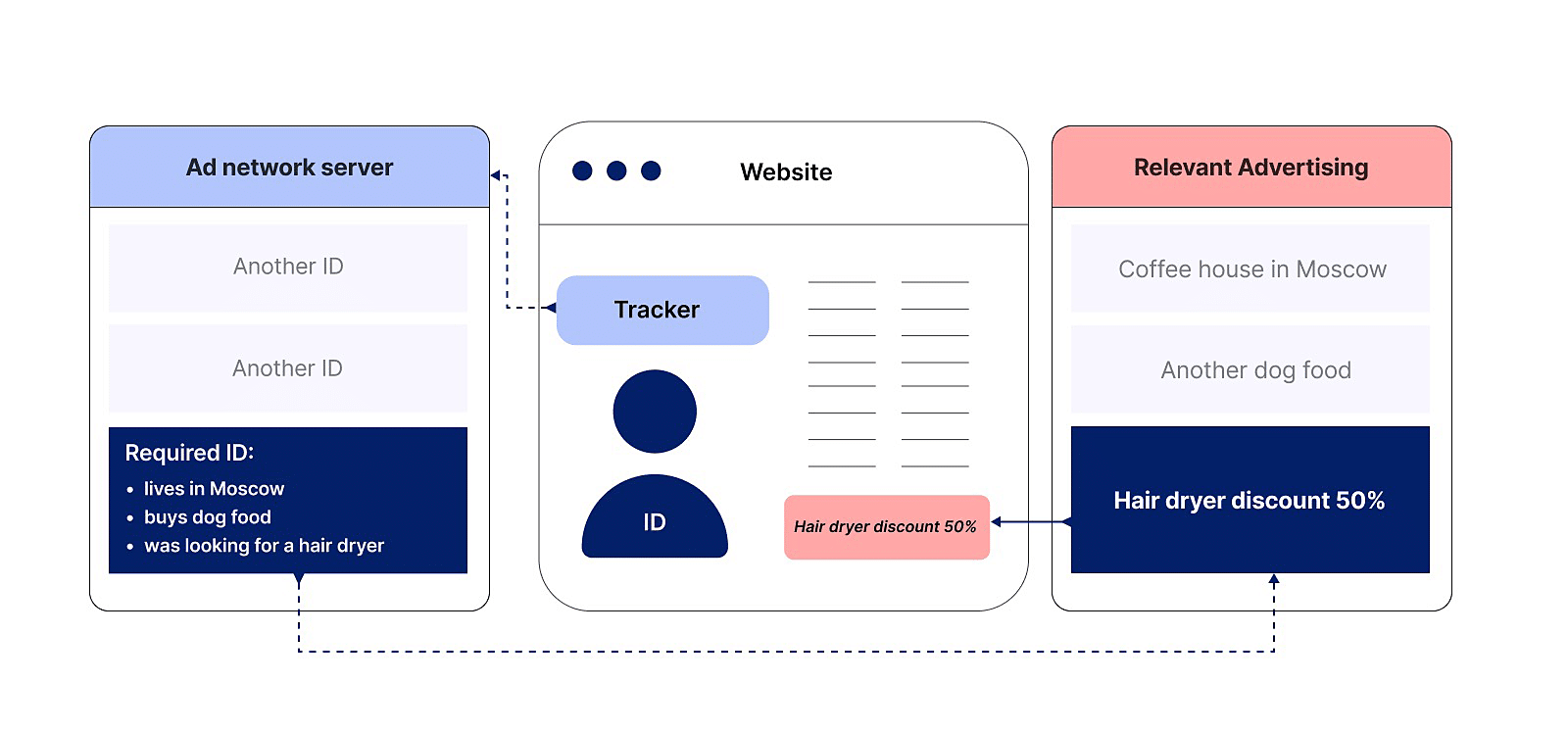
We will write more about how cookies work in ads in a different article.
Problem: browsers started to ban third party cookies
Yandex Browser, Firefox and Safari have stopped sending cookies to the third-party systems. Chrome is planning to do the same in 2023. Browsers want to protect their users from frauds who can steal their personal data and passwords through tracking systems.
The ban affects cookie-file ads only. The ad networks won’t be able to install their trackers on sites, collect users' data and show them personalized ads after this ban.
Solution: users' identification without cookies
Developers suggest using unique identifiers without cookies to solve this problem. It’s also called Web 3.0 identifiers: they’re a philosophical part of the new 3-d internet generation.
We wrote more about what the future of the internet would look like with examples of services already built on the principles of Web 3.0 in this article «Web 3.0: the internet evolution from one-page sites to meta universes».
There are lots of ways to identify users without cookies and here’s some of them.
A unique fingerprint of the FingerprintJS browser. It tracks the user’s browser and device.

FingerprintJS library requests user’s browser and device settings: installed plugins, screen size and resolution, color depth, operational system, time zone, language. Fingerprint adds Canvas Fingerprint to the received data and forms a 32-bit number — a unique identifier.
This identification method is based on the combination of browser parameters, operation system and graphics equipment which is unique for each device. However, in practice, the Fingerprint doesn’t clearly distinguish one user from another. For instance, all the Apple smartphones of the same model are perceived as a single device: they have the same processor, the same graphics accelerator and the same system library.
The technology has other disadvantages:
- If the user updates the browser, the resulting fingerprint will change. This is a new user from Fingerprint point of view.
- The accuracy is lowered for the 42-nd and older version of Chrome because it stopped activating plugins — they now are shown in Fingerprint.
- Preferences, search history and other information is not available for Fingerprint. This instrument isn’t suitable for ad networks.
Identifier ID5. It allows ad networks to collect data about users and share it among them.

ID5 collects users' data via hashed email addresses, page URLs, IP addresses and timestamps.
This is not a standalone app, rather a network with the connection to the ecosystem. Together, ad networks collect users' data and share it with each other through ID5 identifier. In order to get access to the data, one needs to become an ecosystem partner — through direct integration with ID5 API or through distribution partners.
How ID5 works:
- User visits the site that has the ID5 code.
- The ID5 code generates a unique user’s identifier.
- The encrypted identifier is transmitted to the ad partners that are part of an ecosystem.
- Ecosystem participants decrypt the identifier, identify the user, match the data about this user in their databases and show him relevant ads.
- When the user visits another site which also uses ID5, his identifier is transmitted alongside with the ad query.
Caching ETag (Entity Tag). It helps to identify users via cache ID.
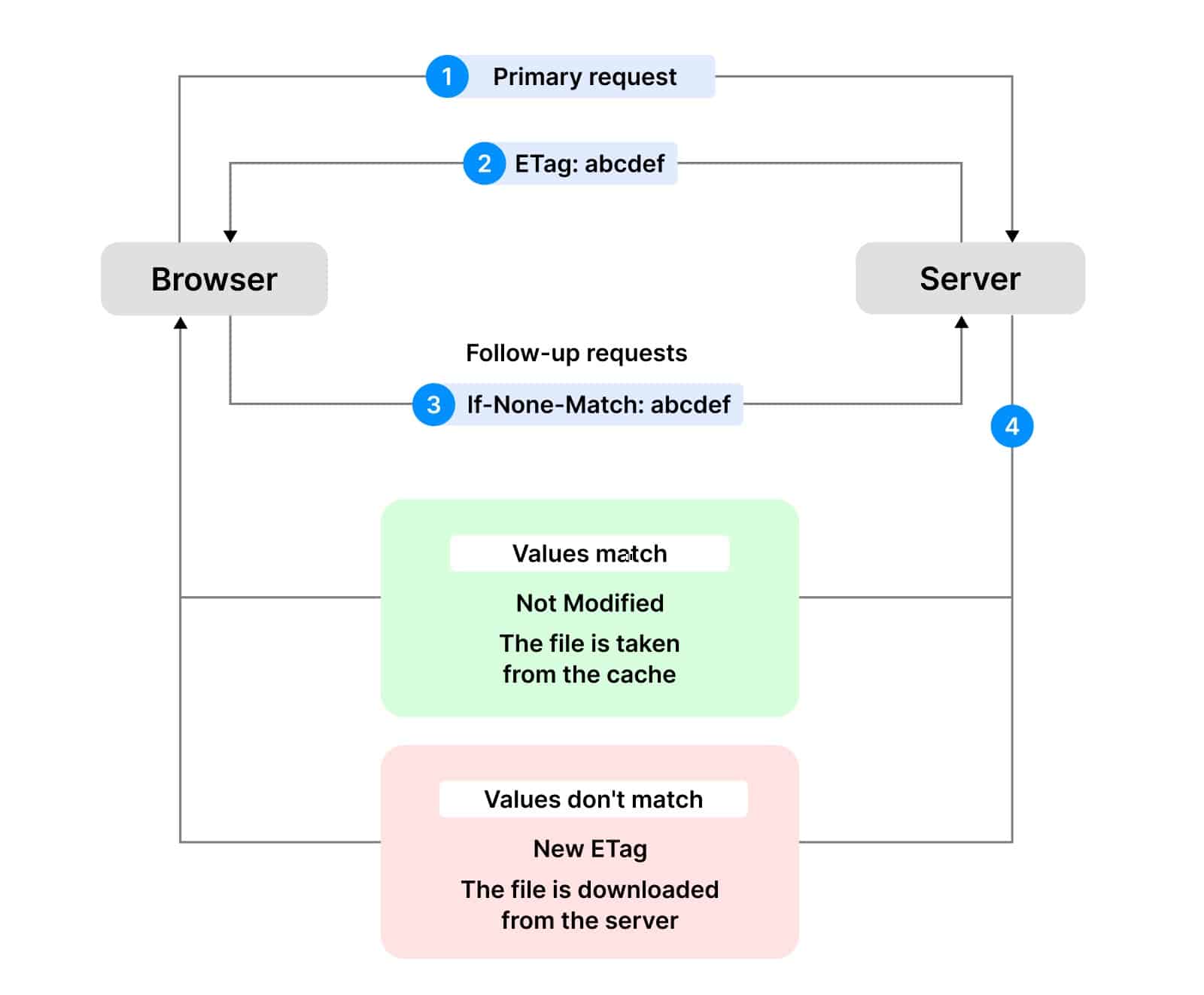
The caching process with using ETag is as follows:
- User visits the site and the browser requests content from the server according to this URL.
- The server sends page content and includes an ETag in the response header — a unique set of characters that corresponds to the current version of the page. E.g., «ETag: abcdef».
- Browser saves ETag and includes it in the request header when making subsequent requests to the server. E.g., «If-None-Match: abcdef».
- The server compares the current page version ETag with what browser transferred. If they match, the server sends a response with the «304 Not Modified» status. It means that the browser can use a cached version of the page. If the set of characters doesn’t match, the server transfers the browser a current version of the page and a new ETag.
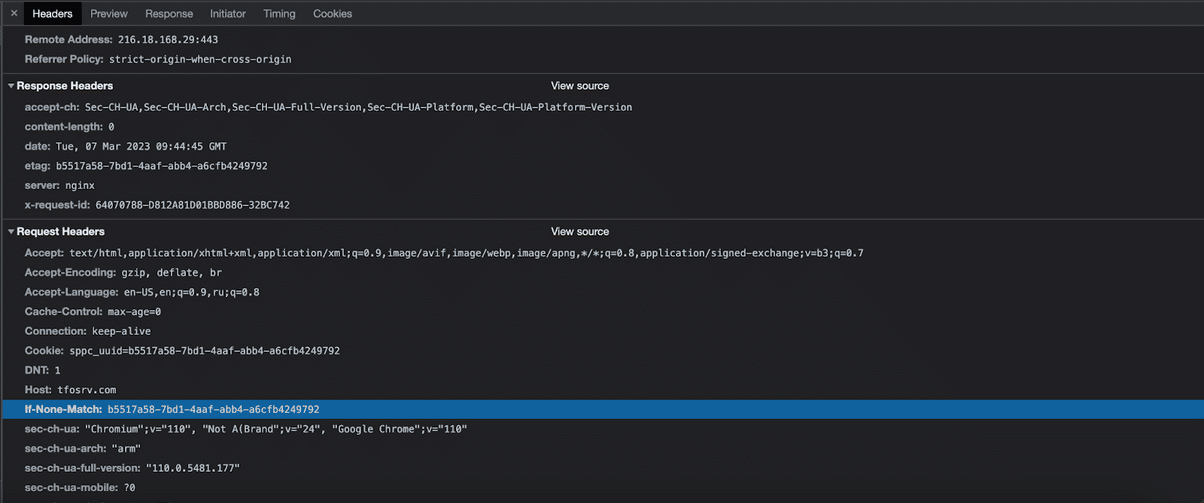
ETag technology doesn’t need third party cookies, yet it’s suitable for collecting data about site users. That is why it’s used by ad networks and system analytics.
How ETag uses the ad networks:
- The user visits the site. If the viewed page is in the browser cache, the HTTP response header of the server contains a unique ETag cache identifier.
- ETag is transmitted to the ad network server. The server uses the parameters it receives to select ads and returns relevant ads.
Conclusion
From our point of view, the ETag technology suits the most for the replacement of the ad network cookies. We’ve been using it in our clients' projects for several years now. Here’s a few reasons why:
- ETag technology is cheaper and it doesn’t depend on third party systems.
- The user can’t delete such cookies.
- This solution is quick to use and implement.
- Only a unique identifier needs to be found. The rest of the user’s data is stored on servers.

